First thought comes to mind when we ask about the cloud, a majority of people would say it is an actual cloud or anything related to weather. Cloud computing is not a new concept in IT field. In simple term, cloud computing is a model which widely available, convenient network access to share pool of computing resources like servers, storage, application with minimal efforts.
Cloud computing involves using internet hosting rather than local severs, to make data and services easily accessible across locations and devices. It is a system where most businesses and people work from more than one computing device. Cloud computing can refer to either the applications or services delivered through the internet as well as to the software and hardware that facilitate these services. Commercial, public cloud services include Amazon’s EC2 (Elastic Compute Cloud), Microsoft’s Azure, and Google’s suite of apps including Gmail, Google Docs, and Google Calendar.

Since 2008, cloud hype has been growing and word spreading about the benefits of the Cloud. Cloud computing is considered by many to indicate a new era in computing – based on access rather than ownership. Cloud features include elasticity, multitenancy, and the potential for maximal resource utilization.
The on demand nature of cloud computing along with high levels of virtualization, automation, easy accessibility and reliable internet than ever before, allows elastic scaling up and minimum resources as needed. Using a pay per use cloud, a business can measure storage and other services as per the volume of business. This has the obvious benefit of not requiring users to invest in high capacity resources without knowing the volume of business ahead of time. Through pooling resources using the internet, services can be utilized more efficiently for both the provider and user.
Types of Cloud Computing
Cloud computing itself has different forms, as per different needs and in different situations.
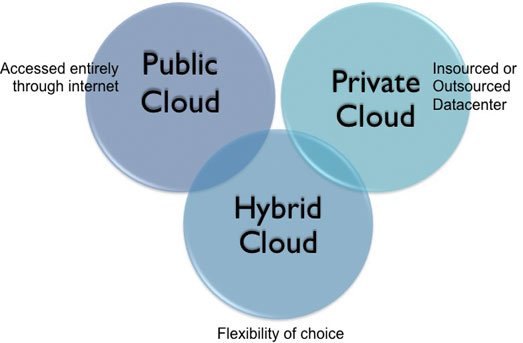
- Private cloud services exist solely by an organization which either manages the service itself, or has it managed by a third party. The examples discussed above all refer to versions of public clouds, accessible to the public and managed by a host organization, which sells these services.
- Community clouds are shared by several organizations with a community that may share goals or concerns. Government or G-Cloud is a specialized example of this – one agency may provide a cloud service to a variety of other agencies under the same organizational umbrella.
- There are also hybrid clouds, which combine public and private offerings to allow information exchange and even application compatibility across many different and disparate cloud service offerings. Hybrid cloud and its ability to utilize third party cloud providers makes this type of cloud especially flexible, and perfect for scaling to different needs.
Cloud computing Models
There are three primary service delivery models for cloud computing. The three models are often referred to together as the SPI model.

- Software as a Service, or SaaS: In this model, the user, client or consumer runs an application from a cloud infrastructure. Through an interface such as a web browser, the client or user may access this application from a variety of devices. The complete application is offered as on demand service. This saves the client from having to invest in any software licenses or servers up front, and can save the provider money since they are maintaining and providing only a single application. In this model, the client does not manage cloud infrastructure, networks or servers, storage, or operating systems. Even, Microsoft, Google, and Zoho offer SaaS.
- PaaS or Platform as a Service: This model involves software encapsulated and offered as a service, from which higher levels of service may then be built. The user, customer, or client in this model is the one building applications which then run on the provider’s infrastructure. This in turn provides customers and clients with the capability to deploy applications onto the cloud infrastructure using programming tools and languages, which the provider supports. The customer still does not manage the framework, network, servers or operating system, but has control over deployed applications and sometimes over the hosting environment itself. Some examples of Platform as a Service include Google’s App Engine or Force.com
- IaaS stands for Infrastructure as a Service. Basic storage and computing capabilities are, in this model, offered as standardized services through the network. This model shares servers, networking equipment, storage systems, and other elements, making them available to handle workloads. The customer is then provided with the ability to rent processing, storage, networks and other computing resources, and is able to deploy and run software – including applications and operating systems. Again, the customer is not managing cloud infrastructure, but in this case, the customer does control operating systems, deployed applications, storage, and sometimes-certain networking components. Some examples of this model include Amazon, GoGrid, and more.
A gradation exists over these three models – the more integrated model, SaaS provides the highest level of security since it is unambiguous that the service provider is responsible for security measures. PaaS, and IaaS, offer degrees of flexibility for clients to develop their own software, leave more gaps in security unless the user takes security into their own hands.
For many reasons, cloud computing is being hailed as the indicator of a new era in computing. According to the Global Industry Analysts report, the cloud computing market will reach 127 billion dollars by 2017. For the reasons discussed and more, cloud computing possesses an allure to the business and technology world that will probably not go away, or probably even be called into question, anytime soon.
However, cloud computing has a number of potential drawbacks – notably that of privacy and control of information. Privacy and security are inherent challenges in cloud computing because their very nature involves storing unencrypted data on a machine owned and operated by someone other than the original owner of the data.
Issues arise from lack of data control, lack of trust of all parties with access, uncertainty about the status of data (whether it has been destroyed when it should, or whether there has been a privacy breach), and compliance with legal flow of data over borders.
The nature of the risks of course, varies in different scenarios, depending among other things, on what type of cloud is being employed. These concerns are serious enough, for example, that public clouds are generally not used at all for sensitive information. Privacy issues in cloud computing includes:
- Data protection: Data security plays an important role in cloud computing environment where encryption technology is the best option whether data at rest or transmitted over the internet. Hard drive producers are supplying self-encrypting drives that provide automated encryption, even if you can use encryption software to protect your data. If we talk about security of transmitted data, then SSL encryption is the best option to secure your online communications as well provides authentication to your website and/or business that assures the data integrity and the users’ information is not altered during transmissions.
- User control: This can be both a legal issue and one raised by consumers themselves. SaaS environment offers the control of consumers’ data to the service provider so; data visibility and control will be limited. In that case, there is a threat of data stolen, misused or theft, as consumers have no control over cloud. Even data transparency is missing for example, where the data is, who owns it, and how it is being used. However, data exposure can also be possible during data transferring as many countries have implemented the law of accessing data if they found it distrusting.
- Employee training and knowledge: A full understanding of when cloud services should and be used needs to be a part of basic employee training in many jobs that involve managing information. Due to lack of training people may not understand the impact of decisions related privacy they generally made.
- Unauthorized usage: This can includes usage of data ranging from targeted advertising, to the re-sale of data on the cloud. The service provider may gain income from secondary usage of data. Agreements between clients and providers must be specific about unauthorized usage as it will enhance the trust and lessen the security worries.
- Loss of legal protection: Putting data on the cloud can involve a loss of legal protection of privacy. It can be impossible to follow all the legislation for a cloud computing for example, with Canada’s privacy act or health laws. Other policies such as the U.S Patriot Act as mentioned above, can actually force exposure of data to third parties. Different locations have many different laws to protect (or in some cases infringe on) the privacy of these users. Data in the cloud is, at best, extremely unclear in terms of locality. At worst, the nature of this ambiguous and instantaneous data flow across borders can make privacy laws impossible to enforce.
Cloud computing, inarguably holds immense potential for ease of use, convenience, scaled expenses, and is a hard to resist tool for businesses. Cloud computing eliminates many of the financial risks that had previously been inherent to doing business digitally. It provides a platform for sharing information globally, in an age where most business involves global elements. Along with mobile devices, and increasingly reliable internet, cloud computing is another step in pulling down distance between the business and teamwork. The plus sides are many.
The End of Theory
However, the risks and ambiguity currently inherent to the cloud indicate that more innovation is needed, mostly on the part of providers. Agreements between clients and providers need to be specific about these issues, especially unauthorized use. Federal governments need to enact laws that are designed to stay relevant and protect consumers in the age of the internet. Instead of trying to enforce laws from an earlier era, new laws must be created which are designed to accommodate the uncertainties of cloud computing, and widespread internet use in general.
This does not absolve users and clients of responsibility. Training at every level is necessary. Employees, who are in charge of keeping data secure, as well as those who may deal with these issues in passing. Must understand the inherent risks involved with cloud computing as well as steps that can be taken on the user side to mitigate these risks.
1 thought on “Security and Privacy Issues in Cloud Computing”
Comments are closed.